Vulnerability and Threat Management
Vulnerability management in refers to the systematic process of identifying, classifying, prioritizing, remediating, and mitigating software vulnerabilities. It’s an ongoing process that helps protect a system or network from cyber-attacks. In an era where cyber threats are ever-evolving, the ability to identify and address vulnerabilities promptly is critical. It serves as a proactive measure to prevent breaches before they occur, safeguarding sensitive data and maintaining operational integrity.
Vulnerability management spans across all aspects of an organization’s IT infrastructure. This includes, but is not limited to, network equipment, servers, applications, databases, and cloud services. It involves continuous monitoring and assessment to ensure all systems are up-to-date and protected against known vulnerabilities. It’s not just about patching software; it’s about understanding the entire ecosystem of your IT environment and ensuring it’s resilient against potential cyber threats.
Threat management in cybersecurity refers to the identification, assessment, and prioritization of potential threats that could compromise the security of an organization. It involves understanding and mitigating threats posed by external sources, such as hackers, malware, and other cybercriminal activities. By effectively managing threats, an organization can reduce the likelihood of successful cyber attacks, thereby protecting its assets, reputation, and stakeholders. Effective threat management not only identifies and neutralizes threats but also anticipates future risks, allowing for timely and strategic responses.
The key perspective here is that while vulnerability management focuses on weaknesses within the organization’s systems and processes, threat management deals with potential or actual external malicious activities aimed at exploiting the vulnerabilities found in all organisations. It’s a more outward-looking approach that requires constant vigilance and adaptation to the ever-changing landscape of cyber threats.
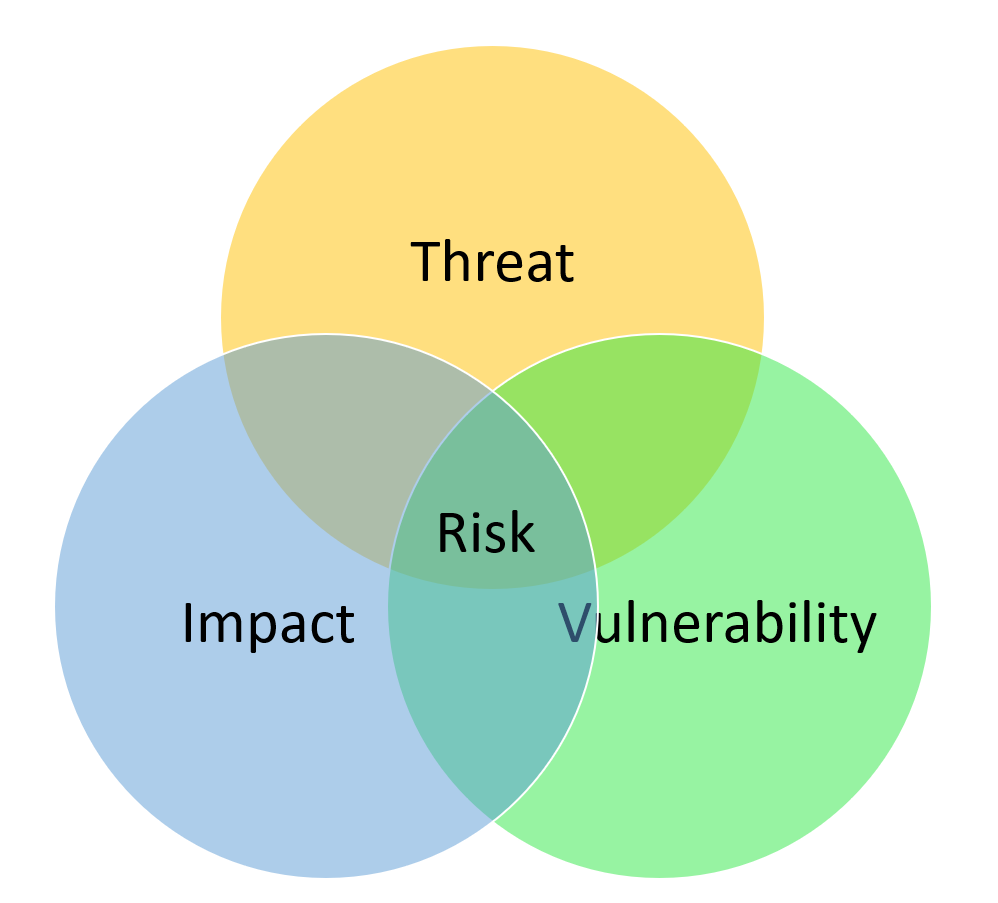
Combining an approach that considers external threats, and the organisation’s internal vulnerabilities, and undertaking a business impact assessment, we reach a risk assessment that allows us to prioritise our mitigation efforts.
Introduction to Vulnerability Management
Vulnerability Management is a critical practice in cybersecurity, focused on the identification, evaluation, treatment, and reporting of security vulnerabilities in systems and the software that runs on them. It is an essential discipline for the protection of systems, networks, and data from cyber breaches and attacks. By identifying and addressing vulnerabilities before they can be exploited by attackers, organizations can significantly reduce their risk profile. This process is not just about fixing flaws; it’s about understanding and managing the risks associated with these vulnerabilities.
In the constantly evolving landscape of cyber threats, where new vulnerabilities are discovered daily, a robust vulnerability management process is indispensable. It serves as the backbone of an organization’s cybersecurity defenses, ensuring that potential security holes are identified and patched in a timely manner.
Overview of Regular Assessments and Patch Management:
- Regular Assessments:
- Regular vulnerability assessments are a cornerstone of effective vulnerability management. These assessments involve scanning systems and applications to identify vulnerabilities.
- The goal is to create an inventory of vulnerabilities and understand their potential impact on the organization.
- Assessments should be conducted regularly and following any significant changes to the IT environment (like new system deployments or updates).
- Patch Management:
- Patch management is a critical component of the vulnerability management process. It involves the systematic notification, identification, deployment, installation, and verification of patches in systems and software.
- Effective patch management ensures that vulnerabilities are patched before they can be exploited by cybercriminals, thereby maintaining the integrity and security of the systems.
- This process requires a coordinated effort across various teams within an organization and should be part of an ongoing security strategy, rather than a one-time event.
Developing a successful vulnerability management program requires a tailored approach that aligns with the specific needs, context, and risk profile of an organization. A one-size-fits-all solution does not exist in the realm of cybersecurity due to the unique nature of each organization’s infrastructure, resources, and threat landscape. Tailoring the program ensures:
- Resource Optimization: The organization allocates its resources efficiently, focusing on the areas of greatest risk and impact.
- Relevance: The strategies and tools used are relevant to the specific technologies and systems in use.
- Regulatory Compliance: The program aligns with industry standards and regulatory requirements relevant to the organization.
- Organizational Culture: The program is designed to fit within the existing culture and operational workflows, ensuring better adoption and effectiveness.
Steps to Identify, Assess, and Mitigate Vulnerabilities:
A well-structured vulnerability management program is crucial for maintaining the cybersecurity posture of an organization. Key steps in developing such a program include:
- Identification of Vulnerabilities:
- Use of automated vulnerability scanning tools to regularly scan systems and networks.
- Staying informed about new vulnerabilities through security bulletins and advisories.
- Conducting manual reviews and assessments to supplement automated tools.
- Assessment of Vulnerabilities:
- Prioritizing identified vulnerabilities based on factors like severity, exploitability, and potential impact on the organization.
- Understanding the context of vulnerabilities to determine the true risk they pose to the organization.
- Engaging stakeholders across departments to gain a comprehensive view of the security posture.
- Mitigation of Vulnerabilities:
- Implementing patches or updates to rectify known vulnerabilities.
- Applying security configurations and best practices to reduce the risk of exploitation.
- In cases where immediate patching is not feasible, employing compensatory controls like firewalls, intrusion detection systems, or segmentation to mitigate risk.
- Continuous Improvement:
- Regularly reviewing and updating the vulnerability management process to incorporate new threats, technologies, and organizational changes.
- Promoting a culture of security awareness to ensure all staff understand their role in maintaining cybersecurity.
- Conducting post-incident reviews to learn from any breaches or near-misses and refine the vulnerability management approach accordingly.
- Establishing Roles and Responsibilities
- Leadership and Oversight: Assign a leader or a dedicated team to manage and oversee the vulnerability management program, ensuring accountability and efficient execution.
- Role Definition: Clearly delineate roles and responsibilities across different departments and personnel involved in the program, such as IT, security, operations, and others.
- Training and Awareness: Continuously educate and update all relevant team members about their roles in the program, emerging threats, and best security practices.
- Defining Processes and Workflows:
- Vulnerability Identification: Set up a consistent and comprehensive process for the detection and reporting of vulnerabilities using various tools and methods.
- Risk Assessment and Prioritisation: Establish criteria and procedures for evaluating and ranking vulnerabilities based on their severity, exploitability, and potential impact.
- Remediation and Mitigation: Outline clear steps and protocols for addressing identified vulnerabilities, including patching, configuration updates, and alternative safeguarding measures.
- Documentation and Reporting: Implement a robust documentation and reporting system for tracking vulnerabilities, actions taken, and the effectiveness of those actions.
- Integration with Other Security Practices:
- Alignment with Security Policies: Ensure that the vulnerability management program is in harmony with the organization’s broader security policies and goals.
- Collaboration with Incident Response Teams: Seamlessly integrate the program with incident response mechanisms to facilitate quick action in the event of a breach.
- Continuous Monitoring and Improvement: Keep the program dynamic and adaptable, incorporating new tools, technologies, and practices as they arise in the cybersecurity field.
- Feedback Loops: Establish channels for ongoing feedback and improvement, allowing the program to evolve based on practical experiences and emerging threats.
Components of Vulnerability Management
A robust vulnerability management program consists of several key components, each playing a vital role in ensuring the effectiveness of the overall strategy:
1. Vulnerability Scanning Schedule:
- Importance: Regular vulnerability scanning is essential for timely identification of security weaknesses. It helps organizations stay ahead of potential threats by providing insights into their current security posture.
- Best Practices:
- Frequency: Scans should be conducted regularly, with the frequency determined by the organization’s risk profile and the nature of its assets. Critical systems may require more frequent scans.
- Comprehensive Coverage: Ensure scans cover all assets, including networks, servers, applications, and endpoints.
- Use of Automated Tools: Employ automated scanning tools for efficiency, but complement them with manual reviews for thoroughness.
2. Patch Deployment Strategies:
- Effective Patch Management Techniques:
- Prioritization of Patches: Based on the severity and exploitability of vulnerabilities, prioritize patches to address the most critical issues first.
- Testing Before Deployment: Test patches in a controlled environment before widespread deployment to minimize the impact on system stability.
- Automated Patch Deployment: Where possible, use automated tools to streamline the deployment process, ensuring timely and consistent patch application.
3. Incident Response Procedures:
- Preparing for and Responding to Vulnerabilities:
- Incident Response Plan: Develop a comprehensive plan detailing how to respond to security incidents resulting from vulnerabilities.
- Team Training: Ensure the incident response team is well-trained and equipped to handle potential breaches.
- Regular Drills: Conduct regular drills to test and refine the incident response procedures.
4. Vulnerability Remediation Tracking:
- Methods to Track and Ensure Remediation:
- Remediation Workflow: Establish a clear workflow for tracking the remediation process from identification to resolution.
- Use of Management Tools: Implement vulnerability management tools for tracking and reporting on remediation efforts.
- Accountability Measures: Assign clear accountability for each step of the remediation process to ensure that vulnerabilities are addressed in a timely manner.
Introduction to Threat Management
Understanding threat management is crucial for an effective cybersecurity strategy. This section explores the definition of threat management, how it contrasts with vulnerability management, and the inherently external nature of threats in the cybersecurity landscape.
Definition and Contrast with Vulnerability Management
Threat Management: In the realm of cybersecurity, threat management refers to the practices and processes used to identify, assess, and mitigate potential external threats to an organization’s IT infrastructure. These threats can include various forms of cyber-attacks such as hacking, malware, phishing, and more.
The key distinction between threat and vulnerability management lies in their focus and approach. While vulnerability management is concerned with identifying and addressing weaknesses within an organization’s systems and networks, threat management focuses on external factors that could exploit these vulnerabilities. This includes preparing for, detecting, and responding to malicious activities originating outside the organization.
The External Nature of Threats in Cybersecurity
Threats in cybersecurity typically originate from external sources and are often driven by malicious intent. These threats are dynamic and constantly evolving, as cybercriminals develop new tactics and strategies to exploit vulnerabilities in IT systems. Understanding this external nature is vital for organizations to develop effective defensive strategies. It requires constant vigilance and a proactive approach to monitor, detect, and counteract these external threats.
Understanding the Threat Landscape
A crucial aspect of effective cybersecurity is comprehending the threat landscape. This section delves into the various types of cyber threats, their impact on organizations, and the motives and tactics employed by cybercriminals.
Types of Cyber Threats and Their Impact on Organizations
The cyber threat landscape is diverse, with numerous types of threats posing significant risks to organizations. Some of the common types include:
- Malware: Malicious software including viruses, worms, trojans, and ransomware, designed to damage or disrupt systems.
- Phishing: Fraudulent attempts to obtain sensitive information such as usernames, passwords, and credit card details through deceptive emails or websites.
- Denial-of-Service Attacks: Attempts to make a machine or network resource unavailable to its intended users, often by overwhelming it with traffic from multiple sources.
- Data Breaches: Unauthorized access and retrieval of sensitive data, leading to privacy violations and potential financial losses.
The impact of these threats can be profound, ranging from financial losses and reputational damage to legal consequences and operational disruptions. It’s essential for organizations to understand these threats to implement effective defensive measures.
The Motives and Tactics of Cyber Criminals
Cybercriminals often have diverse motives, including financial gain, espionage, political agendas, or simply causing disruption. Understanding these motives is key to anticipating and mitigating potential attacks.
Their tactics are constantly evolving, utilizing sophisticated methods to exploit vulnerabilities. This includes advanced social engineering techniques, exploiting zero-day vulnerabilities, and leveraging emerging technologies such as artificial intelligence and machine learning for malicious purposes.
Staying informed about the changing tactics and motives of cyber criminals is vital for organizations to continuously adapt their cybersecurity strategies and remain resilient against these threats.
The management of these threats not only involves the deployment of technical solutions like firewalls and antivirus software but also includes staying informed about the latest cyber threat trends and implementing comprehensive security policies and training programs. This holistic approach is necessary to safeguard an organization’s digital assets against the ever-changing landscape of cybersecurity threats.
Key Methodologies in Threat Management
Effective threat management incorporates a range of methodologies designed to identify, assess, and mitigate potential cybersecurity threats. This section highlights key methodologies including threat intelligence, threat modeling, vulnerability assessments, penetration testing, and incident response planning.
Threat Intelligence
Threat Intelligence involves collecting and analyzing information about emerging threats and cyber attacks. This proactive approach helps organizations stay ahead of potential threats by understanding the tactics, techniques, and procedures (TTPs) of adversaries. Effective threat intelligence allows for better informed decision-making in cybersecurity strategies.
Threat Modeling
Threat Modeling is a structured approach to identifying and prioritizing potential threats. It involves simulating scenarios to understand and manage risks. Popular frameworks in threat modeling include:
- STRIDE: An acronym for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege, focusing on categorizing threats.
- PASTA: The Process for Attack Simulation and Threat Analysis, a seven-step, risk-centric methodology.
- VAST: The Visual, Agile, and Simple Threat modeling approach, which is scalable and integrates with agile methodologies.
- Other frameworks tailored to specific organizational needs and contexts.
Vulnerability Assessments
Vulnerability Assessments are critical in identifying weaknesses in an organization’s security posture. This method involves a systematic review of security weaknesses, providing insights into areas that require strengthening to prevent potential breaches.
Penetration Testing
Penetration Testing, or ethical hacking, involves simulating cyber attacks to test an organization’s defenses. It’s a hands-on approach that helps to identify vulnerabilities that could be exploited in a real-world attack, providing practical insights into the effectiveness of existing security measures.
Incident Response Planning
Incident Response Planning is essential in preparing for and managing cyber incidents. It involves developing a structured approach to detect, respond to, and recover from cyber attacks. A well-prepared incident response plan minimizes the impact of attacks and is a crucial component of organizational resilience.
For those seeking a deeper understanding of vulnerability and threat management, I encourage reading the in-depth discussion available in the book where I provide detailed insights, case studies, and practical strategies to enhance your knowledge and skills in cybersecurity. The book serves as a valuable guide for cybersecurity professionals, IT staff, and anyone interested in strengthening their organization’s defence against cyber threats.
