While technical controls such as firewalls are often seen as the first line of defence, with the perimeter of business systems becoming more and more blurred, technical controls alone cannot be perimeter-based. Here we briefly look at the different options for security technology to inform your strategy, but bear in mind that technology changes swiftly and new solutions come into fashion quickly as the threat landscape mutates.
Cybersecurity Technical Solutions can roughly be divided into two groups, Preventative and Detective controls (Although some cross this divide). Preventative solutions are designed to block particular activities, whereas detective controls are designed to detect malicious activities. Let’s have a look at some of them and how they can be employed. Below I will take you through how business systems architecture can be designed using security systems to improve business security. I use a hospital as an example, your network would obviously be different.
Network Topology and Security system implementation.
Best practice in Network Architecture design is to segregate networks so that sensitive business systems do not sit on the same network segment as business systems that are “at risk”, whether that is between internet-facing systems or internal systems. Several solutions can be implemented. Consider below the basic network topology. We have implemented several preventative solutions to segregate the business network of a hospital. Using Firewalls internally and externally, and on certain devices, we are effectively blocking the traffic except for “Allowed” traffic. We are then subdividing the networks using VLANS on network switches because there is no reason for HR to be able to access Finance systems etc. This effectively limits an intruder to only the systems on the same subnet. If someone in HR clicked on a phishing email, a bad actor would not automatically have access to Finance systems. We could just as easily have achieved these network segments using something called a “Software Defined Network” (SDN) which can dynamically change the network configuration based on a set of rules.
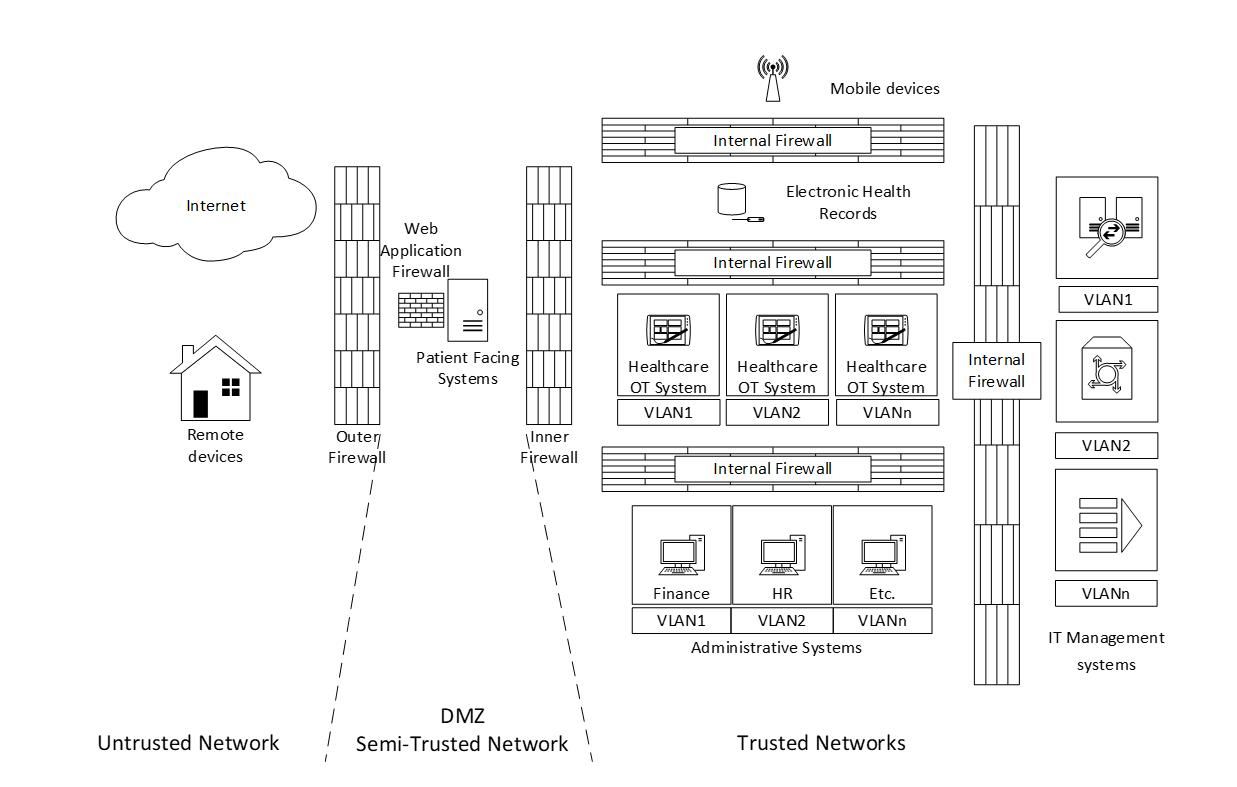
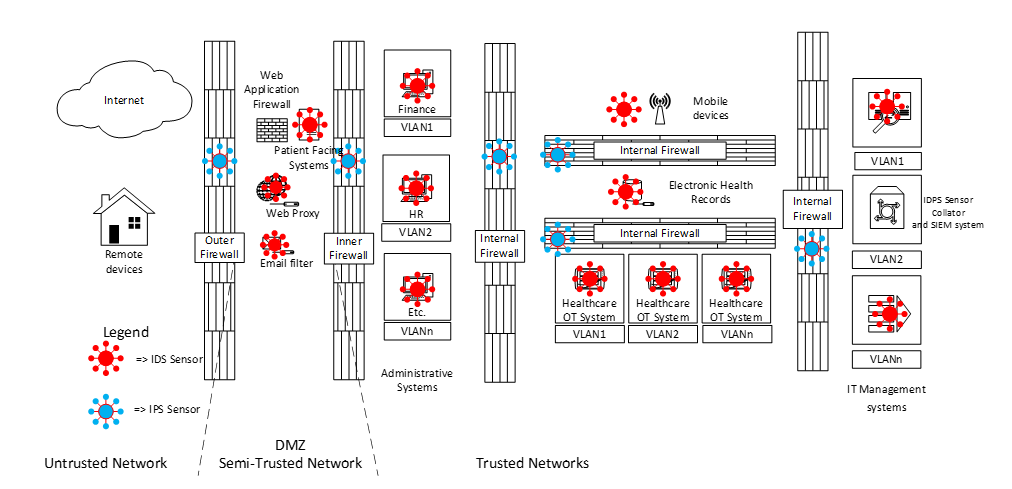
The next thing we should consider is the placement of Intrusion Detection Systems (IDS) which are detective controls that send alerts and Intrusion Prevention Systems (IPS) which are similar, but actively block malicious traffic once detected. These can be host-based to detect intruders on sensitive equipment, or network-based to detect over-the-network malicious traffic. Best practice recommends the implementation of IPS on firewalls and IDS within network segments or directly on sensitive equipment. These go back to a well-protected collator that could include SIEM (Security information and event management) systems and SOAR (Security orchestration, automation and response) systems, which as the names suggest, collect and collate security information and orchestrate a response (Automated or pass it on to the Incident Response team).

The next thing to consider is the placement of outbound web proxies, which is something that manages outbound connections from users, allowing them to safely browse the internet whilst blocking malicious outbound traffic (intruder applications beaconing to a command and control server for example) We also need to consider inbound traffic via email, and the placement of email filters. You can also see that we have moved certain systems further back in the architecture, further isolating them from intruders.
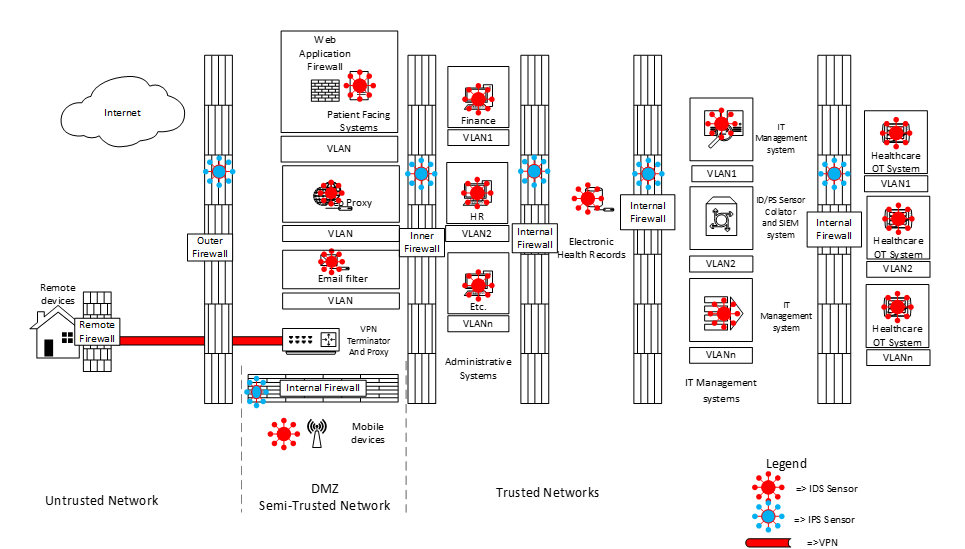
At this point, we’ve implemented most of our technologies. It’s time to do a risk assessment and also check that we haven’t overlooked anything. It appears we forgot to protect remote devices and give them capabilities to access internal systems. Because the remote devices are less trusted, we will implement a VPN that terminates in the DMZ and put a proxy to allow them to access internal systems in a controlled manner. Our risk assessment also shows two further risks that can easily be mitigated: Mobile devices are unlikely to need full access to business systems, and since they are regularly on the open internet, let’s move the mobile device network into the DMZ. Further, the OT (Operational Technology) systems such as MRI scanners etc. are highly sensitive, and unlike IT systems, they tend to not have system patches updates as regularly and therefore are often less secure than IT systems. Let’s move these systems to the most secure location within the network.
Our final Architecture design process is to consider communication requirements between systems sources, destinations ports etc. By doing this, we can clearly define the network access within the system. For simplicity’s sake, I have not included connectivity requirements for the IDS/IPS systems, nor the connectivity requirements for the IT Management systems, which depend on what systems are in place (Such as Antivirus consoles, patch deployment systems and configuration management systems)
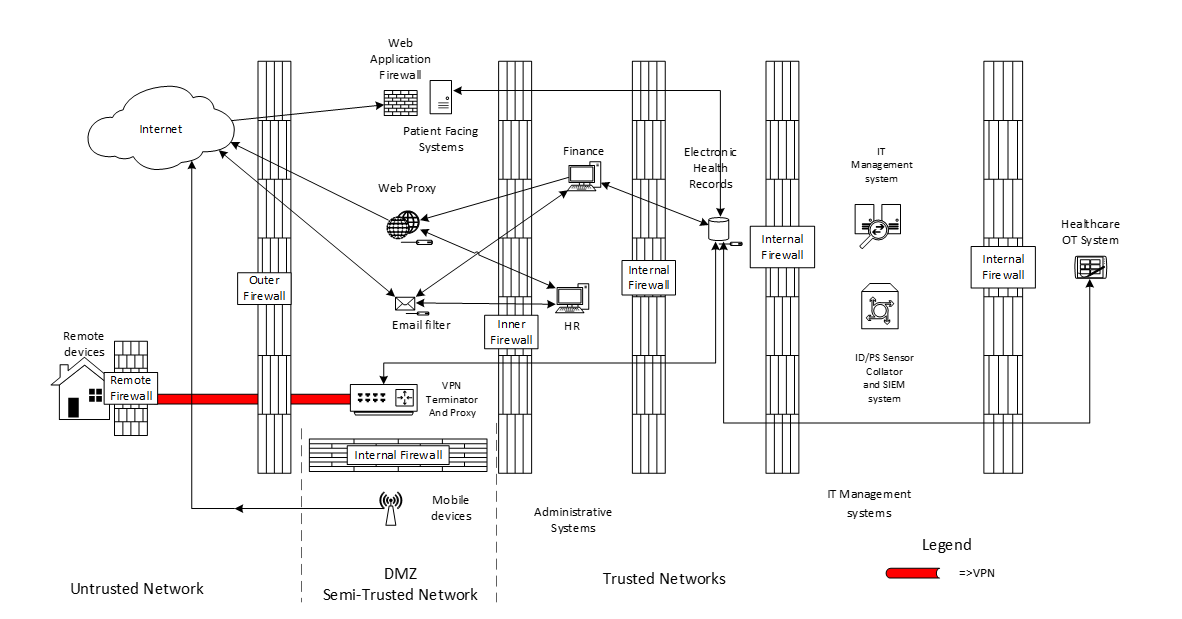
Your security architecture is now configured. We have used the following components, your Security Governance should reflect this in a set of policies and standards.
- Firewalls (Internal, external and host-based.
- DMZ capable Switches
- SDN architecture if desired
- IDS and IPS, both host-based and network-based
- Web Proxies
- Email Filters
- VPN’s
The example used does not include cloud-based infrastructure, if your systems include cloud, you also need to consider the following:
- Cloud Access Security Brokers
- Secure Cloud Configurations
- Container Security
- Data Protection and Data Loss Prevention
- Compliance and Governance
- The shared responsibility model.
