The ultimate goal of Cybersecurity is to ensure that resources are only accessed by entities that legitimately should have access to them. Identity and Access Management (IAM) is a comprehensive framework used to manage and secure digital identities within an organisation’s IT infrastructure. IAM focuses on ensuring that the right individuals have the appropriate access to the right resources at the right time, while also mitigating the risks associated with unauthorised access.
Below I will briefly introduce relevant topics, but to be sure, I go into them in far more detail in my book.
Let’s look briefly at some concepts in play here.
Identity:
During identification, a subject presents their identity to the system using various means. This can involve typing a username, swiping a smart card, waving a token device, speaking a specific phrase, or utilizing biometric characteristics like facial recognition, fingerprints, or handprints. These actions serve as a means of asserting the subject’s claimed identity to the system. NIST SP 800-63-3 has defined 3 Identity Assurance Levels (IAL) as below.
- IAL1: There is no requirement to link the applicant to a specific real-life identity. Any attributes provided in conjunction with the authentication process are self-asserted or should be treated as such (including attributes a Credential Service Provider, or CSP, asserts to an RP).
- IAL2: Evidence supports the real-world existence of the claimed identity and verifies that the applicant is appropriately associated with this real-world identity. IAL2 introduces the need for either remote or physically-present identity proofing. Attributes can be asserted by CSPs to RPs in support of pseudonymous identity with verified attributes.
- IAL3: Physical presence is required for identity proofing. Identifying attributes must be verified by an authorized and trained representative of the CSP. As with IAL2, attributes can be asserted by CSPs to RPs in support of pseudonymous identity with verified attributes.
Authentication
Authentication is a critical process that involves verifying the identity of a user or system before granting access to resources in an IT environment. Authentication is fundamental to IAM because it ensures that users are who they claim to be. This process often involves credentials like usernames and passwords, but can also include more sophisticated methods like biometric scans or multi-factor authentication. By effectively authenticating users, IAM systems help maintain security, prevent unauthorized access, and ensure that the right individuals have access to the appropriate resources within an organization.
Authentication is different to identity because it confirms to the system the identity of a user or entity attempting to access a system or resource.
There are various authentication methods available, each with its own strengths and weaknesses. Some common authentication techniques include:
- Password-based authentication
- Multi-factor authentication (MFA)
- Biometric authentication
- One Time Passwords (OTP)
- Certificate-based authentication
- Hardware Token (FIDO2 e.g. YubiKey)
Authorisation
Authorisation is a critical component of access management that governs the permissions and privileges granted to authenticated users within an organisation’s digital environment. It involves determining what resources, systems, and data an individual or a group of users can access and the actions they can perform within those resources, some key terms here are:
- Access Controls, including:
- Role-Based Access Control (RBAC)
- Attribute-based Access Control (ABAC)
- Discretionary Access Control (DAC)
- Mandatory Access Control (MAC)
- Rule-Based Access Control (RuBAC)
- Principle of Least Privilege, based on the idea that users should only have access to the resources and functionality required to perform their specific job functions, which would include access rights analysis, access control design and access management practices.
- Segregation of Duties, where the goal is to prevent any single person from having complete control over a sensitive process or function, thereby reducing the risk of errors, fraud, and misuse of privileges.
- Privileged Access Management, a set of security practices, policies, and technologies designed to manage and control privileged accounts and their access to critical systems, sensitive data, and administrative privileges within an organisation’s IT infrastructure.
- Access Control Policies, a framework for managing user privileges, enforcing security measures, and ensuring compliance with regulatory requirements, the framework would include Access Review, Monitoring and Auditing of access rights.
Accountability
Accountability refers to the principle of holding individuals or entities responsible for their actions and activities within an organisation’s systems and resources. Accountability ensures that actions taken by users can be traced back to them, enabling transparency, trust, and the ability to investigate and address any security incidents or policy violations. it would include concepts such as:
Auditing and logging of user activities. This involves capturing and recording detailed information about user actions, which can be used for transparency, investigation, and compliance purposes. Auditing involves systematically examining and evaluating user activities to verify compliance with policies, regulations, and best practices. Logging, on the other hand, refers to the process of recording user activities in a log file or database. This includes capturing information such as timestamps, user identities, accessed resources, and performed actions.
Accountability and Compliance Management plays a vital role in ensuring compliance with regulatory requirements and internal policies. By establishing clear access control policies and procedures, organisations can define the rules and guidelines for user authorisation.
Deterrence of Malicious and Unauthorised Activities. By implementing robust accountability measures, organisations create a culture of transparency and responsibility. Users understand that their actions are being monitored and that there are consequences for inappropriate or unauthorized activities. This knowledge acts as a strong deterrent, discouraging individuals from engaging in malicious actions or attempting to exploit their access privileges.
Administration
Administration is the management of user accounts, including the creation, modification, and deletion of user identities and access privileges. This involves user provisioning, deprovisioning, and ongoing access management based on changes in roles, responsibilities, or employment status. Proper administration is essential for maintaining the integrity and security of an organisation’s systems and data. It ensures that user accounts are managed in a timely and accurate manner, reducing the risk of unauthorised access or data breaches. By aligning user access with the principle of least privilege, administration contributes to a more secure environment and helps protect against potential threats or insider attacks.
- Provisioning, Provisioning involves the creation of accounts and their associated access rights within an organisation. This involves registration and verification processes, user onboarding, access rights assignment, group membership, and authentication configuration (Such as password changes and complexity, multifactor authentication enrollment etc).
- Maintenance involves regular access reviews to ensure the ongoing accuracy and appropriateness of access rights assigned to users. The goal of maintenance is to verify and validate access privileges, promoting the principle of least privilege and reducing the risk of unauthorised access within an organisation’s systems and resources.
- Deactivation or Deprovisioning, typically involves account deactivation, access rights revocation, data and credential management, account termination and removal and documentation and audit trail recording.
Federation
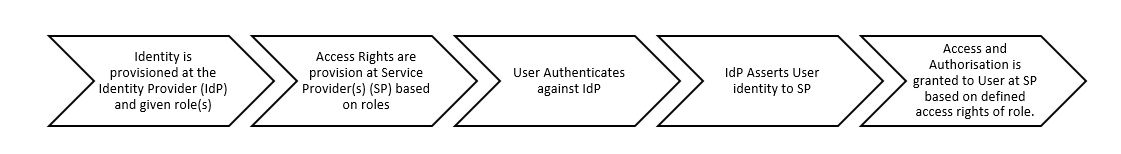
Federation (often referred to as “Single Sign On”) allows a user to authenticate themselves once with their identity provider (IdP), which is typically their home organisation or a trusted third-party service. The IdP then asserts the user’s identity to the service provider (SP), which is the system or application the user wants to access. This authentication process is typically based on industry-standard protocols like Security Assertion Markup Language (SAML) or OpenID Connect.
Governance
The main objectives of identity governance are:
- Identity Lifecycle management
- Access Request and Approval management
- Segregation of Duties enforcement
- Access Control management strategy
- Continuous Monitoring and Certification
- Audit and Compliance
- Risk Mitigation
IAM Best Practices
Sources of IAM Best Practice can be found here:
- ISO/IEC describes an access management framework in ISO/IEC 29146:2016 and separately an identity management framework in ISO/IEC 24760-1:2019 and ISO/IEC 24760-2: 2015 and section 9 of ISO27002:2013 discusses access control.
- NIST describes Digital Identity Guidelines in the SP800-63 series, SP800-53r5 describes IAM in section 3.7, the Cybersecurity Framework provides guidelines in the Identify and Protect functions..
- Cloud Security Alliance (CSA) offers various resources and frameworks related to IAM in cloud environments. Their Cloud Control Matrix (CCM) and Security, Trust & Assurance Registry (STAR) provide guidelines and best practices for secure identity and access management in cloud computing.
- Information Systems Security Association and The Identity Defined Security Alliance are professional organisations that offers valuable resources, including white papers, webinars, and conferences, covering various aspects of IAM best practices. They provide insights and recommendations from industry experts and practitioners.
- Identity and Access Management Solutions Providers: Vendors and solution providers in the IAM space often publish best practice guides, case studies, and white papers to help organisations implement effective IAM strategies. Examples include Okta, One Identity, and ForgeRock, among others.
- Industry Conferences and Events: Attending industry conferences and events focused on cybersecurity, IAM, or identity governance and administration (IGA) can provide opportunities to learn about best practices from industry leaders, experts, and peers. These events often feature sessions, workshops, and panel discussions on IAM-related topics.
- Professional Security Organizations and Forums: Participating in online forums and communities, such as the Identity and Access Management Professionals (IAML) community or relevant subreddits, can provide a platform to discuss IAM best practices, share experiences, and learn from others in the field.
