Incidents are inevitable. No matter how robust your security measures are, there is always a possibility of a breach or an attack that can disrupt your systems, compromise your data, or jeopardise your organisation’s reputation. Incident response is the structured process of identifying, managing, and resolving security incidents in a timely and effective manner.
Multiple approaches to Incident Response exist.
NIST SP800-61r2 describes a 4-step cycle:
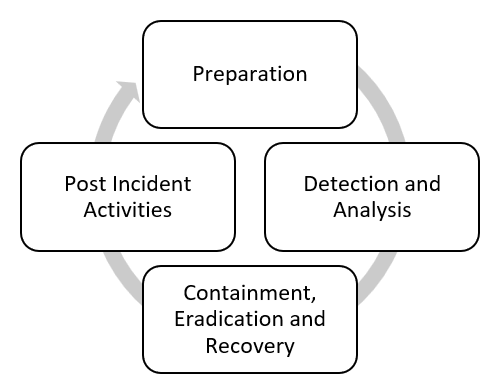
The ISO/IEC 27035 Series describes a 5 step cycle:
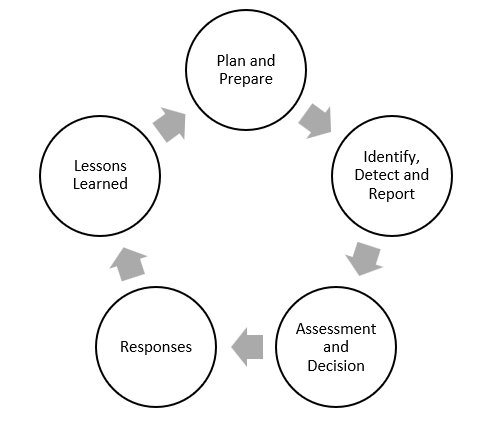
For this section though, we will briefly examine incident response using the SANS 6 steps
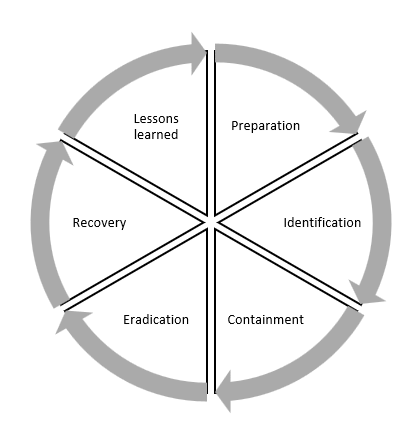
Of course, Incident Response is a critical phase, and I know I keep mentioning it, but I do go into this in-depth in my book.
Preparation
This is a critical phase of the Incident Response cycle, as it lays the foundations that ensure the organisation is well-equipped to handle cybersecurity incidents. It involves the following critical tasks:
- Creating an Incident Response Team: Assembling a team with diverse skills in cybersecurity, IT, legal, and communications. Each member’s role must be clearly defined.
- Defining Roles and Responsibilities: Assigning specific tasks such as initial response, investigation, and communication to relevant team members.
- Conducting Risk Assessments: Identifying potential threats and vulnerabilities that could impact the organization.
- Developing an Incident Response Plan: Crafting a comprehensive plan that outlines procedures for detecting, responding to, and recovering from incidents.
- Implementing Security Controls: Establishing safeguards like firewalls, intrusion detection systems, and encryption to prevent incidents.
- Training and Awareness: Regularly training staff on security best practices and their roles in incident response.
- Creating Documentation: Developing clear documentation for the incident response process, including contact lists, action plans, and reporting templates.
- Testing and Updating the Plan: Regularly testing the incident response plan through drills and updating it based on lessons learned and evolving threats.
Identification
In the Identification phase of the Incident Response cycle, the primary goal is to detect and identify potential security incidents. The effectiveness of this phase lies in the ability to swiftly recognize and evaluate any anomalies or suspicious behaviors in the IT environment, which are potential signs of a cybersecurity threat.
Critical steps in the Identification phase of incident response include:
- Continuous Monitoring: Vigilantly monitoring network traffic and system logs to detect unusual activities or anomalies.
- Analysis of Alerts: Systematically analyzing alerts generated by security tools to identify potential security incidents.
- Using of Intrusion Detection Systems: Employing intrusion detection systems to identify potential threats or IOCs.
- Event Correlation: Correlating data from various sources to discern patterns indicative of a security incident.
- Initial Assessment: Quickly assessing identified anomalies to determine their potential impact and whether they constitute a security incident.
- Documentation and Reporting: Documenting and reporting initial findings for further investigation or action.
Containment
In the Containment phase, the focus shifts to preventing further damage following a security incident. This stage is vital for stabilizing the environment and preventing further compromise while preparing for the subsequent phases of incident response.
Critical steps in the Containment phase include:
- Isolating Affected Systems: Segregating compromised systems or networks to prevent the spread of the incident.
- Shutting Down Compromised Accounts: Deactivating accounts that have been breached to block unauthorized access.
- Implementing Temporary Fixes: Applying quick fixes or patches to mitigate the immediate threat.
- Enhancing Monitoring: Intensifying surveillance to detect any further unusual activity.
- Securing Backup Data: Ensuring backup data is protected and unharmed.
- Communication: Keeping relevant stakeholders informed about the incident and containment efforts.
Eradication
The Eradication phase is pivotal in incident response, aiming to fully remove the threat from compromised systems. This phase is crucial to not only resolve the current incident but also to strengthen systems against similar future threats, ensuring long-term security and resilience.
Critical steps in the Eradication phase include:
- Root Cause Analysis: Conducting a thorough investigation to understand the underlying cause of the incident.
- Eliminating Malicious Elements: Identifying and removing all components related to the threat, such as malware or unauthorized access points.
- Patching Vulnerabilities: Applying updates or patches to fix vulnerabilities exploited in the incident.
- Updating Security Measures: Enhancing security protocols and tools based on findings from the incident.
- Verification: Ensuring that all aspects of the threat have been completely removed.
- Documentation: Recording the eradication process for future reference and compliance purposes.
Recovery
In the Recovery phase, the goal is to restore affected systems, networks, and data to normal operation. The phase focuses on re-establishing normal operations and ensuring critical services of the organization are functioning as expected, bringing the organization back to its full operational capacity post-incident.
Critical steps in the Recovery phase include:
- Restoring Systems: Reinstating affected systems and networks from clean backups.
- Reconfiguring/Rebuilding: Reconfiguring or completely rebuilding compromised systems to ensure they are secure.
- Validation: Checking the integrity and functionality of the recovered environment to ensure no remnants of the threat remain.
- Monitoring Post-Recovery: Keeping an eye on the systems for any signs of anomalies that might indicate unresolved issues.
- Re-establishing Normal Operations: Gradually bringing all operations back to their standard functional state.
- Review and Analysis: Conducting a post-incident review to understand the effectiveness of the recovery process and identify areas for improvement.
Lessons Learned
The final phase, “Lessons Learned,” is crucial for enhancing future incident response capabilities. This phase involves a thorough analysis of the entire incident response process to identify strengths and weaknesses. The ultimate goal is to not only improve response strategies for future incidents but also to implement measures that could prevent similar occurrences.
Key activities in the “Lessons Learned” phase include:
- Post-Incident Review: Conducting a comprehensive review of the incident and response process.
- Documentation of Lessons Learned: Recording insights and learnings from the incident.
- Updating Plans and Procedures: Revising the incident response plan and related procedures based on the insights gained.
- Training and Awareness: Updating training programs to include new learnings.
- Implementing Improvements: Applying changes to prevent future incidents or improve response strategies.
- Communication: Sharing the findings with relevant stakeholders.
These activities are essential to continually improve incident response capabilities.
