IT Security Strategy Management
In my book “Securing The Cyber Realm” I wrote of 9 areas you need to address when creating your IT Security Strategy. I strongly recommend that you read the book, but I will briefly cover these here:
Select a topic below
Risk Management
IT Risk management involves the identification, assessment, and prioritization of potential risks to the organization’s information technology systems, applications, and data. It helps organizations understand the potential impact of security incidents and make informed decisions about risk mitigation strategies.
The thesis for my Master’s Degree was a quantitative analysis of the steps required for defining the scope of a Zero Trust deployment project. Based on publically available data, I was able to show that good Risk Management protocols are 4 times more effective at breach prevention than all of the other scoping operations. This is perhaps unsurprising, but this outcome underscores the importance of this step.
Here are some of the key components of IT Risk management:
- Risk identification: Identifying potential risks to the organization’s IT systems, applications, and data.
- Risk assessment: Assessing the likelihood and impact of identified risks.
- Risk prioritization: Prioritizing risks based on their likelihood and impact, and allocating resources accordingly.
- Risk mitigation: Developing and implementing mitigation strategies to reduce the likelihood and impact of identified risks.
- Risk monitoring and review: Monitoring the effectiveness of risk mitigation strategies and reviewing the risk management process regularly.
IT Risk management is an essential component of a cybersecurity program as it provides a structured approach to managing security risks, and helps organizations make informed decisions about the allocation of resources and investment in security controls.
We have only discussed IT Risk Management briefly on this page, but it certainly needs deeper insight, I encourage you to take a look at our IT Risk Management page for further information on Risk Management.
Vulnerability and Threat Management
This is related to, but not the same as, Risk Management. However, in cybersecurity, vulnerabilities and threats are closely interconnected, and understanding their relationship is essential for effective risk management.
Vulnerability Management
Regular vulnerability assessments and patch management are essential components of a robust cybersecurity strategy. They are critical tools for identifying and addressing security vulnerabilities to maintain a secure environment. By following established processes, leveraging appropriate tools, and integrating threat intelligence, organisations can effectively mitigate risks, protect their systems and data, and stay resilient against emerging threats.
Developing a comprehensive vulnerability management program tailored to organisational needs is essential for effectively identifying, assessing, and mitigating vulnerabilities. By focusing on these key aspects, organisations can develop a comprehensive vulnerability management program tailored to their specific needs. This program will enable them to identify vulnerabilities, assess their impact, prioritise remediation efforts, and effectively manage the risks associated with vulnerabilities in their systems and applications.
The key steps in developing a vulnerability management program are
- Establish roles and responsibilities
- Define processes and workflows
- Align with other security practices
- Implement the key components:
- Vulnerability Scanning Schedule
- Patch Deployment strategies
- Incident Response procedures
- Vulnerability Remediation Tracking
Threat Management
Threat Management takes an opposing view. Whilst vulnerabilities are related to the organisational infrastructure, threats are the external environment within which the organisation operates.
Understanding the threat landscape involves identifying and analysing the various types of cyber threats that organisations face. This includes understanding the motives and tactics of cyber criminals, the types of vulnerabilities that exist in an organisation’s systems and networks, and the potential impact of a successful cyber-attack.
To understand the threat landscape, an organisation should implement the following methodologies:
- Threat intelligence
- Threat Modelling
- Vulnerability assessments
- Penetration Testing
- Incident Response planning
In my book I discuss both Vulnerability and Threat Management in depth.
Cybersecurity Strategy Management
In my book, the third aspect of IT Security Strategy development is Cybersecurity Strategy Management. This may seem strange and a bit of a tautology, but let me explain.
Before you begin developing the Cybersecurity strategy for the enterprise, you need to understand the risks, threats and vulnerabilities that are associated with the enterprise. Risk, threat and vulnerability management have been, up to this point, discovery exercises that help you to describe the landscape that your business operates, the risk appetite of the business and the threat and vulnerability environment that it operates on an within. All of this is informing your Cybersecurity Strategy. This is why I separate IT Security Strategy from Cybersecurity Strategy: IT Security Strategy encompasses all the steps outlined on this page, and is designed to develop our Cybersecurity Strategy. Cybersecurity Strategy, by contrast, is the output of this specific step of the process and it describes a methodology to handle the enterprise cybersecurity needs for all 9 aspects (including itself) of the cybersecurity management program. IT Security Management is a one-time process, Cybersecurity Management is the ongoing process that we describe here. Let’s take a brief look at how it should look:
- Risk Management Strategy – Although you have established the risk appetite of the business and identified the current and foreseeable risks posed to it, your Cybersecurity Strategy should describe the ongoing Risk Management processes. Take a look at our Risk Management page for more insights into Risk Management as an ongoing process.
- Vulnerability and Threat Management Strategy– While you should already have identified the vulnerabilities and threats associated with your business up to this point, threats and vulnerabilities are ever-changing, and you need to develop an ongoing methodology to deal with these two aspects. CISA offer a Vulnerability Management Guide, NIST addresses vulnerability Management in the CSF and SP 800-40 (Although this is primarily directed at Patch Management) and several threat modelling frameworks are STRIDE, PASTA, VAST, Trike and DREAD. You need to choose your methodology and define where, how and how often you review it.
- Cybersecurity Management Strategy – This is the strategy that you are developing here. By putting into a Governance document how your Cybersecurity Strategy is managed, you ensure that your Cybersecurity Strategy stays current and appropriate for the business, given the changes in business strategy over time, the changes in technology and the changes in the threat and vulnerability landscape.
- Technology Management Strategy – As opposed to technology in itself, your Technology Management Strategy describes how your Cybersecurity Technology is managed over time. This would encompass the lifecycle management of your technology assets, the assets it’s designed to protect, and the business processes that the technologies support. Whilst you won’t mention specific technologies (Eg. “CISCO xxxxx”) you might mention technological concepts (Such as SIEM, SOAR, IPS etc.) We will discuss this in more detail in the next section.
- Data Lifecycle Management Strategy – Data is the lifeblood of any organisation that uses Information Technology. It’s absolutely critical that you address the data lifecycle including how data is created, classified, stored, processed, shared and disposed of, and what compliance requirements surround data handling. We go into this in a little more depth below.
- Identity and Access Management Strategy – IAM describes how users (within and external to your organisation) are Identified, Authenticated, and Authorised. It covers accountability and administration of Identity and Access objects and their lifecycle including provisioning, maintenance and Deactivation or Deprovisioning. Again, e will take a look at this shortly.
- Incident Response Strategy – Unfortunately, the statistics suggest that incidents are inevitable. The incident response strategy discusses how the six stages of incident management are handled: Preparation, Identification, Containment, Eradication, Recovery and Lessons learned. We will look at these in more depth below.
- Education and Training Strategy – Businesses need to run their business, but the employees of that business are also responsible for the cybersecurity culture within the organisation. Whether the business has a laissez-faire attitude towards cybersecurity, or whether everyone is all pulling in the same direction is entirely down to how education is delivered. Education needs to be tailored to different audiences, it needs senior management support, and it needs to be reinforced through different channels. We will look at this in more detail below.
- Cybersecurity Trend Monitoring Strategy – Whilst we have dealt above with ongoing business challenges, technology waits for no one. We have seen recent changes in generative AI, which while it brings multiple benefits to organisations, also brings previously unseen challenges. We are on the verge of having quantum computing that will make short work of current encryption technologies, and on a daily basis, we see new vulnerabilities in widely used products or source codes. Keeping on top of this requires eyes and ears, and most of all, discussion. A trend monitoring strategy will help you identify how the changing technological landscape will impact your organisation. We will finally discuss this below.
Developing a Cybersecurity Strategy is challenging and can sometimes be a bit hit and miss. Cybersecurity can often be seen by senior management as a roadblock to progress, with CS frameworks not bending to business needs. I strongly recommend that you take a look at our COBIT 2019 page. The tailored governance framework that you develop by using COBIT is likely to fulfil your Cybersecurity Governance needs, allowing you to develop a tailored Cybersecurity Strategy that aligns with your Enterprise strategy and changes and adapts over time. You could also take a look at other sources such as NIST Cybersecurity Framework (CSF) ISO 27001, and CIS controls, however, none of these tailor your Cybersecurity Strategy to your Enterprise Strategy in the way that COBIT does, and in fact, COBIT looks to other frameworks to fulfil the needs of organisations.
Technology Management
While technical controls such as firewalls are often seen as the first line of defence, with the perimeter of business systems becoming more and more blurred, technical controls alone cannot be perimeter-based. Here we briefly look at the different options for security technology to inform your strategy, but bear in mind that technology changes swiftly and new solutions come into fashion quickly as the threat landscape mutates.
Cybersecurity Technical Solutions can roughly be divided into two groups, Preventative and Detective controls (Although some cross this divide). Preventative solutions are designed to block particular activities, whereas detective controls are designed to detect malicious activities. Let’s have a look at some of them and how they can be employed. Below I will take you through how business systems architecture can be designed using security systems to improve business security. I use a hospital as an example, obviously your network would be different.
Network Topology and Security system implementation.
Best practice in Network Architecture design is to segregate networks so that sensitive business systems do not sit on the same network segment as business systems that are “at risk”, whether that is between internet-facing systems or internal systems. Several solutions can be implemented. Consider below the basic network topology. We have implemented several preventative solutions to segregate the business network of a hospital. Using Firewalls internally and externally, and on certain devices, we are effectively blocking the traffic except for “Allowed” traffic. We are then subdividing the networks using VLANS on network switches because there is no reason for HR to be able to access Finance systems etc. This effectively limits an intruder to only the systems on the same subnet. If someone in HR clicked on a phishing email, a bad actor would not automatically have access to Finance systems. We could just as easily have achieved these network segments using something called a “Software Defined Network” (SDN) which can dynamically change the network configuration based on a set of rules.
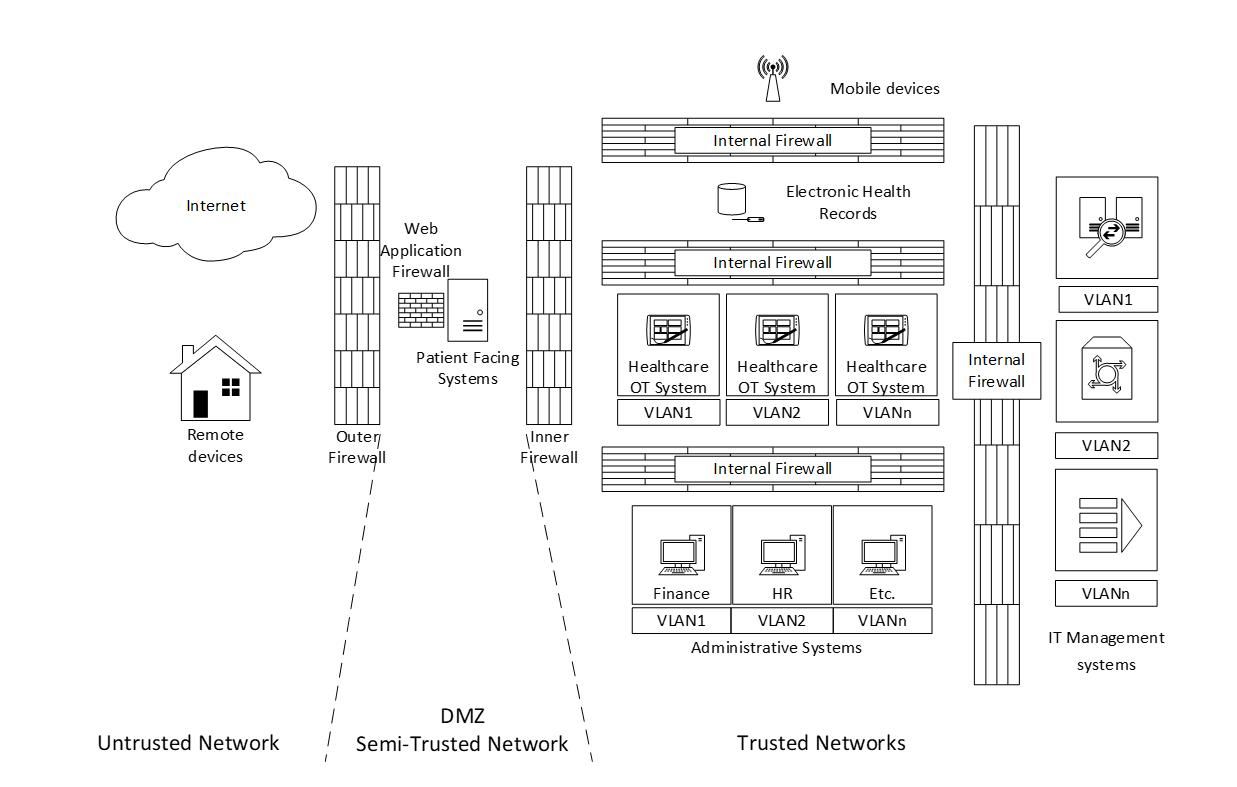
The next thing we should consider is the placement of Intrusion Detection Systems (IDS) which are detective controls that send alerts and Intrusion Prevention Systems (IPS) which are similar, but actively block malicious traffic once detected. These can be host-based to detect intruders on sensitive equipment, or network-based to detect over-the-network malicious traffic. Best practice recommends the implementation of IPS on firewalls and IDS within network segments or directly on sensitive equipment. These go back to a well-protected collator that could include SIEM (Security information and event management) systems and SOAR (Security orchestration, automation and response) systems, which as the names suggest, collect and collate security information and orchestrate a response (Automated or pass it on to the Incident Response team).

The next thing to consider is the placement of outbound web proxies, which is something that manages outbound connections from users, allowing them to safely browse the internet whilst blocking malicious outbound traffic (intruder applications beaconing to a command and control server for example) We also need to consider inbound traffic via email, and the placement of email filters. You can also see that we have moved certain systems further back in the architecture, further isolating them from intruders.
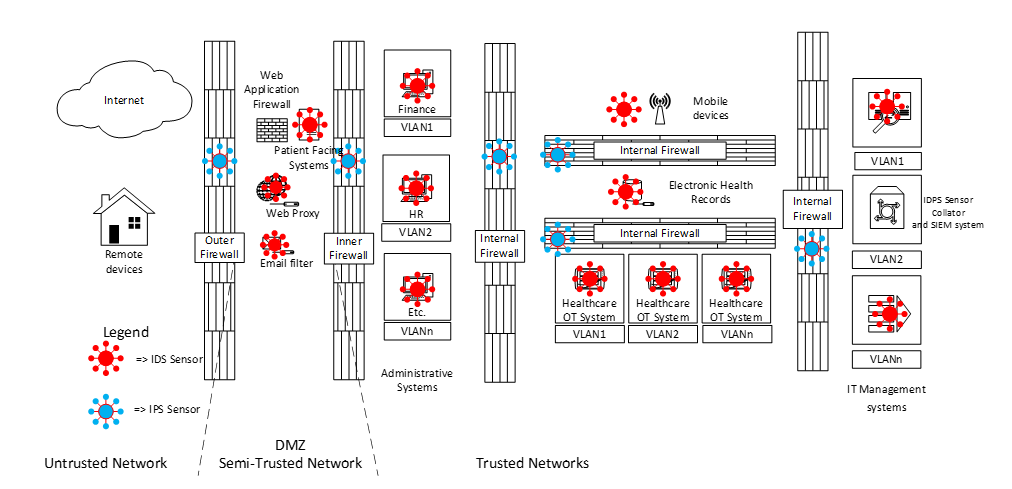
At this point, we’ve implemented most of our technologies. It’s time to do a risk assessment and also check that we haven’t overlooked anything. It appears we forgot to protect remote devices and give them capabilities to access internal systems. Because the remote devices are less trusted, we will implement a VPN that terminates in the DMZ and put a proxy to allow them to access internal systems in a controlled manner. Our risk assessment also shows two further risks that can easily be mitigated: Mobile devices are unlikely to need full access to business systems, and since they are regularly on the open internet, let’s move the mobile device network into the DMZ. Further, the OT (Operational Technology) systems such as MRI scanners etc. are highly sensitive, and unlike IT systems, they tend to not have system patches updates as regularly and therefore are often less secure than IT systems. Let’s move these systems to the most secure location within the network.
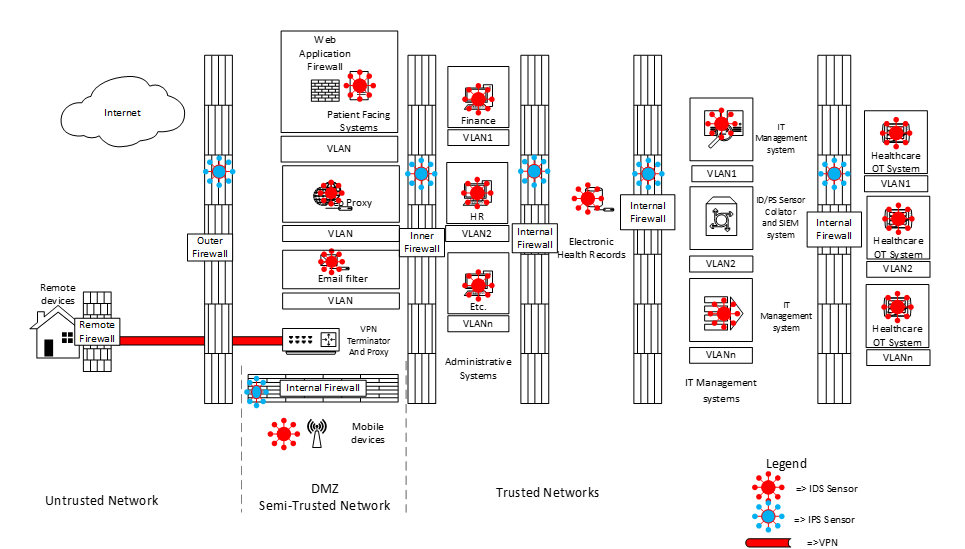
Our final Architecture design process is to consider communication requirements between systems sources, destinations ports etc. By doing this, we can clearly define the network access within the system. For simplicity’s sake, I have not included connectivity requirements for the IDS/IPS systems, nor the connectivity requirements for the IT Management systems, which depend on what systems are in place (Such as Antivirus consoles, patch deployment systems and configuration management systems)
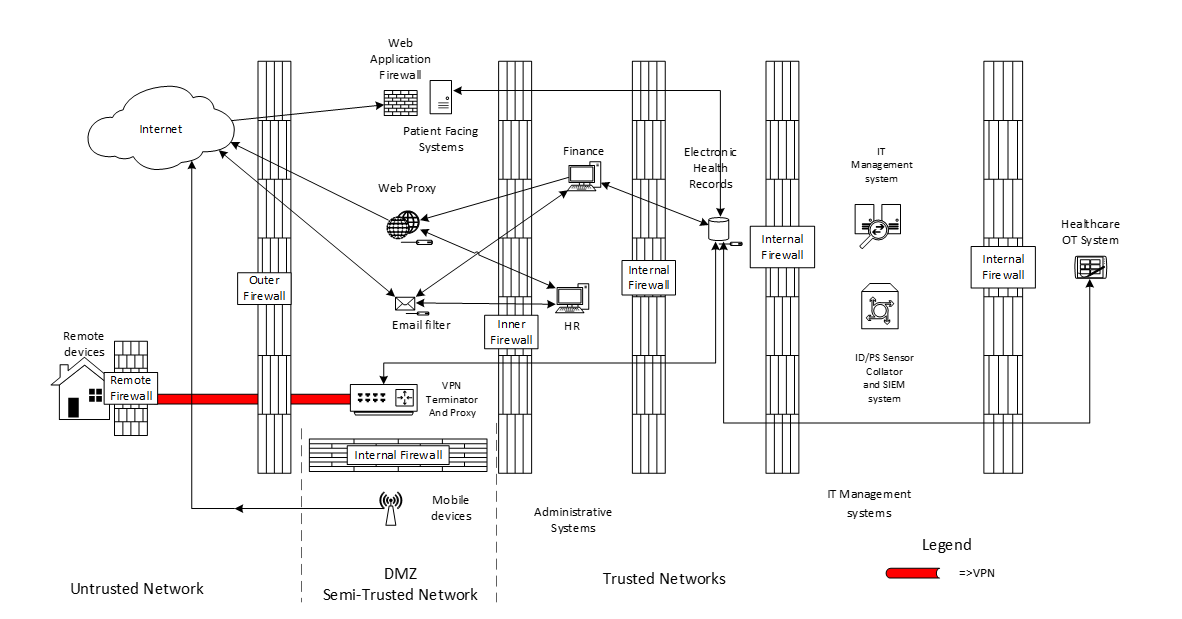
Your security architecture is now configured. We have used the following components, your Security Governance should reflect this in a set of policies and standards.
- Firewalls (Internal, external and host-based.
- DMZ capable Switches
- SDN architecture if desired
- IDS and IPS, both host-based and network-based
- Web Proxies
- Email Filters
- VPN’s
The example used does not include cloud-based infrastructure, if your systems include cloud, you also need to consider the following:
- Cloud Access Security Brokers
- Secure Cloud Configurations
- Container Security
- Data Protection and Data Loss Prevention
- Compliance and Governance
- The shared responsibility model.
Data Lifecycle Management
I have discussed Data Lifecycle management at length on this page and in my book. This is a critical part of securing your business and developing your IT Security strategy.
Here I will briefly mention the core components of Data Lifecycle Management, but strongly encourage you to visit the page linked to above.
Data Classification
Ensuring that your data is properly classified is critical. Data classification is a shortcut to applying appropriate access controls and protection mechanisms as mentioned below.
The main steps to data classification are
- Identify data
- Use Data Governance
- Create Categories
- Prioritise Data
- Define the Resources and Budget
- Keep going
Data Collection and Creation
The first part of the data lifecycle is Data Collection and Creation, and the general rule of thumb is “Only collect data that you need in order to complete the tasks it is needed for.”. The less data you have, the less data you have to protect, and the lower your management overheads.
Data Storage and Transmission
While storing and transmitting data you need to consider access controls and encryption requirements. Implementing a traffic light protocol is an easy way to define encryption and access requirements.
Data Disposal and Destruction
You need to consider data disposal and destruction requirements. That includes both retention policies (whether required by law, for example, by Sarbanes Oxley) or as a business requirement, and data destruction requirements.
Disaster Recovery and Business Continuity
A critical part of Data Lifecycle Management is understanding how to handle the situation when things go wrong. Disaster Recovery is about how to bring a business back online after a disaster, it would include consideration for how much lost data is acceptable, and how long an outage is within the business risk appetite, whereas business continuity relates to how a business will continue to work during and outage (even if at a reduced capacity)
Traffic Light Protocol
We finish with a discussion about Traffic Light Protocol and how we can use this to provide simple and visual management of data.
Identity and Access Management
I discuss this subject in depth on this page, but very briefly, IAM involves the following key components:
- Identification: Establishing the identity of users or entities requesting access to resources by collecting and verifying relevant information, such as usernames, email addresses, or unique identifiers.
- Authentication: Verifying the claimed identity of users through various methods, such as passwords, biometrics, tokens, or multi-factor authentication, to ensure that only authorised individuals gain access.
- Authorisation: Granting or denying access rights to authenticated users based on their roles, responsibilities, and the permissions they require to perform their tasks. This includes defining and managing user roles, access privileges, and entitlements.
- Accountability: Ensuring that user actions and activities are logged, monitored, and audited to provide a clear record of who accessed what resources and when. This supports compliance requirements, investigations, and the identification of potential security incidents.
- Administration: Managing user accounts, including the creation, modification, and deletion of user identities and access privileges. This involves user provisioning, deprovisioning, and ongoing access management based on changes in roles, responsibilities, or employment status.
- Federation: Enabling secure and seamless authentication and authorisation across multiple systems and organisations through the use of trusted identities and protocols. Federation allows users to access resources in different domains without the need for separate credentials for each system.
- Governance: Establishing policies, procedures, and controls to ensure the proper management and oversight of IAM activities. This includes defining access control policies, conducting regular access reviews, and enforcing compliance with regulatory requirements and industry best practices.
Incident Response
The 6 steps outlined by SANS are:
- Preparation: This phase involves proactively establishing an incident response plan and developing the necessary resources, tools, and documentation. It includes tasks such as creating an incident response team, defining roles and responsibilities, conducting risk assessments, and implementing security controls.
- Identification: In this phase, the focus is on detecting and identifying security incidents or events that could potentially lead to a security breach. This includes monitoring systems and networks, analysing logs and alerts, and using intrusion detection systems to identify indicators of compromise (IOCs) or suspicious activities.
- Containment: Once an incident is identified, the next step is to contain it to prevent further damage or spread. This involves isolating affected systems or networks, shutting down compromised accounts, and implementing temporary fixes or mitigations to limit the impact of the incident and prevent it from spreading to other parts of the environment.
- Eradication: In this phase, the objective is to completely remove the threat actor from the compromised systems or networks. It involves conducting a thorough investigation to understand the root cause of the incident, identifying, and eliminating all traces of malicious activity, and patching vulnerabilities or implementing permanent fixes to prevent similar incidents in the future.
- Recovery: Once the incident is eradicated, the focus shifts to recovering the affected systems, networks, and data. This involves restoring systems from clean backups, reconfiguring or rebuilding compromised systems, and validating the integrity and functionality of the recovered environment. The recovery phase also includes re-establishing normal operations and ensuring that the organization’s critical services are functioning as expected.
- Lessons learned: The final phase involves analysing the incident response process and outcomes to identify areas for improvement. This includes conducting a post-incident review, documenting lessons learned, and updating the incident response plan and procedures based on the insights gained from the incident. The goal is to enhance future incident response capabilities and prevent similar incidents from occurring in the future.
Education and Training
Regardless of whether formal training is provided, a “Cybersecurity Culture” exists which reflects the norms, values, knowledge, and beliefs held by the individuals in the organization. When employees lack training, they might fail to understand the importance of cybersecurity, which could lead to the perception that it is irrelevant or a low-priority issue. Similarly, if cybersecurity is seen as “someone else’s problem,” individuals are more likely to behave in ways that perpetuate this belief, resulting in a weak cybersecurity culture that is vulnerable to threats.
Conversely, when employees understand and appreciate the real-world consequences of their actions, they start to develop a sense of responsibility towards cybersecurity. This understanding, combined with a spirit of collaboration, helps instil a positive cybersecurity culture within the organization. Such a culture not only mitigates cybersecurity risks but also promotes an environment of vigilance and proactive threat detection.
I don’t believe that your users are your last line of defence, on the contrary, the people who are creating and using your business infrastructure on a daily basis, with the right cybersecurity culture, can strengthen your cybersecurity posture beyond the capabilities of the technology. As Brice Schnier once said “If you think technology can solve your security problems, then you don’t understand the problems and you don’t understand the technology.”.
Let’s quickly look at this topic, I go into it in depth in my book as well as at a digestible level on this page.
Developing a Comprehensive Training Program
A comprehensive training program is a strategic initiative that aims to enhance the capabilities of employees, ensuring they have the necessary expertise to perform their roles effectively and contribute to the success of the organization. This training program goes beyond the basics and encompasses various aspects, including technical skills, professional development, compliance, and security awareness.
Training Topics – Catering to Different Audiences
In crafting a robust cybersecurity training program, one key consideration is understanding that a ‘one size fits all’ approach will not yield the best results. Different roles within an organization require distinct cybersecurity knowledge and skill sets, and as such, the training content must be appropriately differentiated. By providing tailored training programs for employees, management, IT staff, and cybersecurity professionals, organizations can establish a proactive and security-conscious culture.
Building a Cybersecurity Team
Building a strong cybersecurity team is essential for effective cybersecurity management. Organisations need to have skilled and well-trained cybersecurity professionals who can detect, prevent, and respond to cybersecurity threats.
Understanding Cybersecurity Certifications
Including:
- CISSP
- CEH
- CISM
- CCSP
- Security +
- CCSP
- OSCP
- CIPP
- GIAC
- CRISC
- CISA
- SSCP
- Network +
- CC
Cybersecurity Trend Monitoring
With the constant evolution of technology, cyber threats are also advancing at an alarming pace. To stay ahead of these threats and protect sensitive information, individuals and organizations must adopt a proactive approach to cybersecurity. This is where cybersecurity trend monitoring is important. In this page, I explore the importance of monitoring cybersecurity trends and how it can help safeguard your digital world.
Essential activities for monitoring cybersecurity trends include:
- Following Industry News
- Engage with Cybersecurity Communities
- Attending Conferences and Webinars
- Use Thret Intelligence services
- Build partnerships with your Cybersecurity Vendors
By effectively monitoring Cybersecurity trends, you can benefit your organisation through
- Risk Mitigation: By staying informed about emerging threats, you can identify and mitigate risks before they become significant issues.
- Cost-Efficiency: Proactive cybersecurity measures can save you money in the long run by preventing costly data breaches and security incidents.
- Reputation Protection: Effective cybersecurity trend monitoring helps safeguard your organization’s reputation by preventing security incidents that could damage public trust.
- Strategic Decision-Making: Armed with current cybersecurity insights, you can make informed strategic decisions regarding your organization’s security posture.
Above is a brief outline of what I cover in detail in my book.
Please don’t hesitate to contact me for a consultation about your cybersecurity management needs.
If the book is shown as “Out of Stock” it is likely that you aren’t on your local Amazon site. Change the URL to Amazon.com or Amazon.de or whatever is appropriate.
