Background
IT governance is the framework that brings structure to IT Operations. It explains the methods and techniques the enterprise can implement to execute, monitor, and manage all the IT structures within a company. It gives guidelines and defines the methods to use the IT processes and resources within a company. It also defines the requirements for reporting values and performance measures.
Often thought of as “IT Policies, Standards and Procedures, IT Governance is much more than this, and a properly structured Governance Framework defines the entire IT Organisation.
ISACA, within their COBIT 2019 Framework, define 7 Governance components :
- Processes – organized set of practices and activities giving specific outputs for achieving the objectives.
- Organizational structures – main decision-making entities.
- Principles, policies and frameworks – decode desired behaviour into practical guidance.
- Information – present across the organization needed by the governance and management system.
- Culture, ethics and behaviour – applicable for individuals and organizations, which affects the achievement of governance and management objectives.
- People, skills and competencies – for execution and completion of all activities.
- Services, infrastructure and applications – provides the I&T processing to the governance and management system
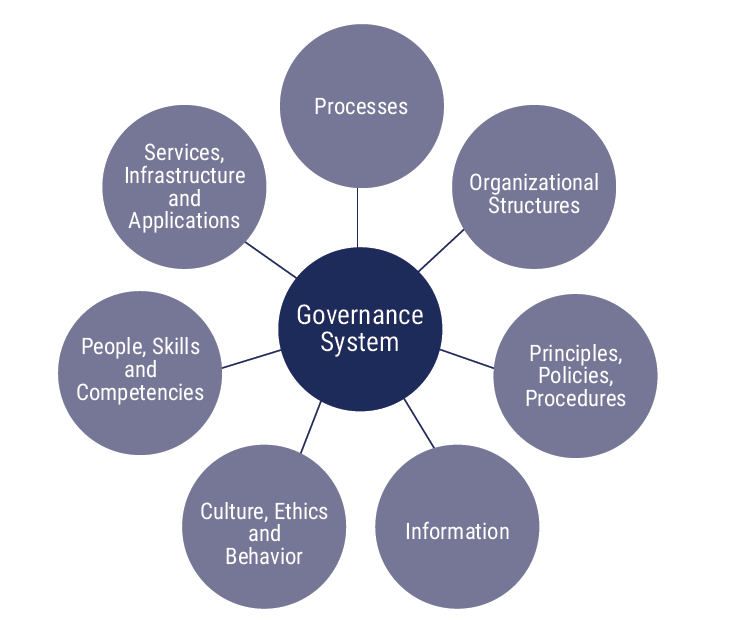
COBIT 2019 IT Governance Components
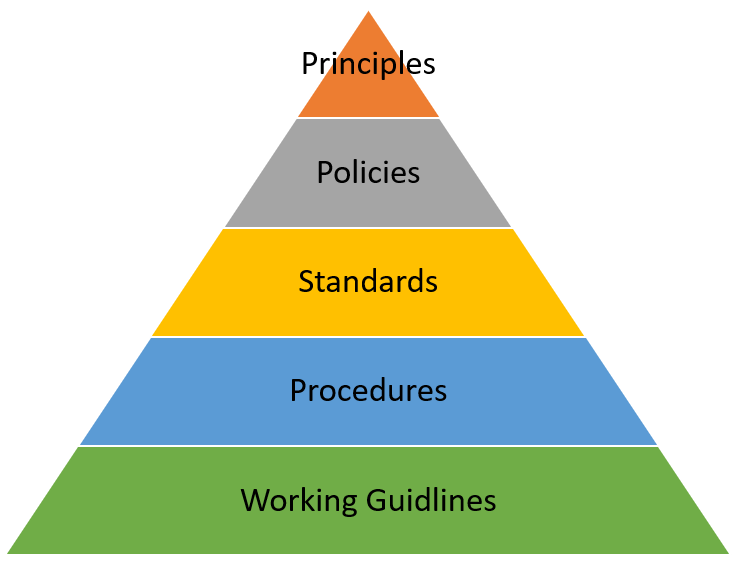
The Policy Pyramid
While the components of the Governance Framework addresses all aspects of the IT environment, the actual documents that make up the Governance System costitutes 5 hierarchical layers, the top 4 layers are intended to be controlled documents, that is, they must go through a controlled change mangement process which is defined within the Governance framework itself.
- Principles – These documents define the strategic environment within which the IT Organisation, along with other Organisational Structures are expected to operate. They define the “Principles” that define the business vision and are mandatory to implement. Examples here might include principles over the use of company information, the protection of personal data and so on.
- Policies – Policies set high-level expectations for the IT organisation, they are intended to answer the question “Why do we need to do this”?
Examples here might be “Access Control Policy”, “Disaster Recovery Policy”, “Risk Management Policy”, “IT Governance policy” - Standards – Assigns quantifiable measures to the IT environment, they are intended to answer “What is Required”? This might include minimum standards for third-party supplier certifications, encryption standards, risk management levels or even outline structures for communications in an Incident Management process.
- Procedure – Establishes the management procedures aligned with business processes. These procedures include information that is intended to answer the question, “How do I do it”? Procedures might include Incident response procedures that state the accountabilities and responsibilities of the incident management process. Data lifecycle procedures that discuss the data management procedures associated with every aspect of the data management life cycle, Change management, Project Management and so on.
- Working Guidelines – These are recommended handling procedures. These documents are aimed at day to day operators of business systems, and may document the instructions on how to achieve a particular thing within a business system, such as how to check whether a backup completed successfully, or what commands to put into a system to obtain a piece of information. Since the working environment is not static and changes regularly, these are intended to be kept updated on a regular basis. Version control is important in this document type, to ensure that everyone is working with the same document.